How common are data breaches?
According to Health IT Security, American Medical Collection Agency (AMCA) was hacked for eight months between August 1, 2018 and March 30, 2019. Since the breach was revealed, at least six covered entities have come forward to report their patient data was compromised by the hack.
AMCA’s parent company has since filed bankruptcy, while other billing services vendor are facing numerous investigations and lawsuits.
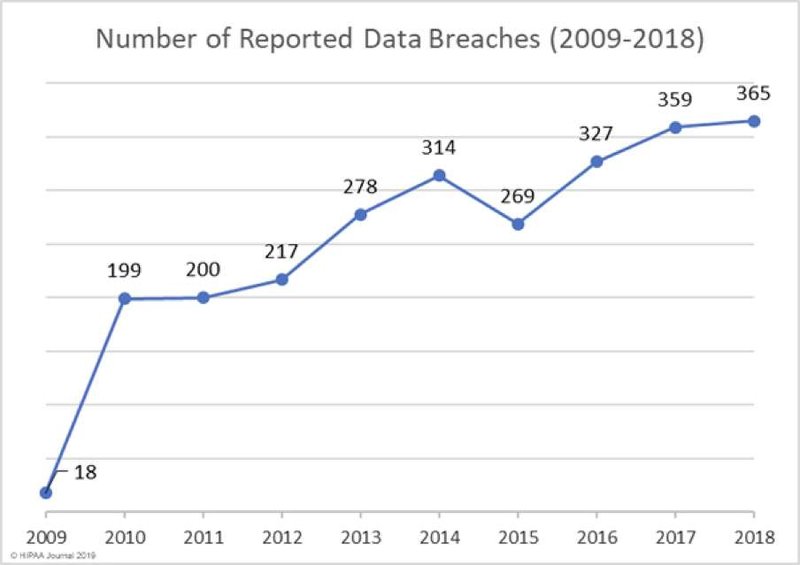
The healthcare industry experiences more breaches than any other sector. In 2018 alone, the industry saw 15 million patient records compromised in 503 breaches.
How do data breaches happen?
Cyber claims received by AIG EMEA (2018) show that 23% of the reported incidents of cyber attacks are of business email compromise, followed by ransomware at 18% and data breach by hackers or due to employee negligence at 14%. Other reasons of breach include impersonation fraud, virus/malware infections, system failure, physical loss or theft and other cyber extortions.
How much is stolen health information worth?
To give context to how valuable this compromised Person Health Information (PHI) is, lets define it. Firstly, PII or personally identifiable information is any data that can be used to contact, locate or identify a specific individual, either by itself or combined with other sources that are easily accessed. It can include information that is linked to an individual through financial, medical, educational or employment records. This values at $2 per individual if stolen.
Now, PHI is regarded to be any health information that is individually identifiable, and created or received by a provider of health care, a health plan operator, or health clearing house. The information might be related to an individual’s present, past or future health, either in physical or mental terms, as well as the current condition of a person. This values at $363 per individual if stolen.
PHI is such valuable and sensitive data because criminals can use it to target victims with frauds and scams that take advantage of the victim’s medical conditions. It can be used to create fake insurance claims, as well as, allowing for the purchase and resale of medical equipment. Other criminals use PHI to illegally gain access to prescriptions for their own use or resale.
Why data security should be a priority?
To begin with cyber crime is costing organizations $11.7 million per year, on average. While taking action is important, waiting for it might be foolish given the costs of cybersecurity are estimated to rise up to $6 Trillion by 2021. 67% of the CIOs think that the possibility that their company will have a data breach or cyberattack this year is given, and 39% of CEOs say that digital transformation is at the top of their agenda already.
On the other hand, global scalability of cybercrime is becoming easier for attackers, as criminals keep on finding new business models and uses of identity theft. Therefore, 55% of the organisations are working together with external partners to reduce security risks and hired security professionals have increased from 25 professionals in 2015 to 40 in 2017 per organisation!
These statistics are proof that it would be dangerous to wait too long and it is important to take action on safeguarding businesses right away. Building a brand takes a lot of time, and cyber crime can tarnish a brand image creating mistrust overnight. In the current time of digitalization, to avoid outages, it is vital to collaborate with an IT company that offers a fully automated, self-learning, and cloud based IT security solution that protects against even the worst cyber threats such as DDoS attacks.
How to ensure data security?
Hacking is a business and usually hackers are looking for the most cost efficient way to get what they want. However, the following steps can help in protecting data for an organisation.
1. User Education and Awareness
Users have a critical role to play in their organisation’s security and so it's important that security rules and the technology provided enable users to do their job as well as help keep the organisation secure. This can be supported by a systematic delivery of awareness programs and training that deliver security expertise as well helping to establish a security-conscious culture.
2. Home and Mobile working
Mobile working and remote system access offers great business benefits but exposes new risks that need to be managed. You should establish risk based policies and procedures that support mobile working or remote access to systems that are applicable to users, as well as service providers.
3. Secure Configuration
Secure configuration refers to security measures that are implemented when building and installing computers and network devices in order to reduce unnecessary cyber vulnerabilities. Security misconfigurations are one of the most common gaps that criminal hackers look to exploit.
4. Removable media controls
Safeguarding against loss via removable media should ideally be planned when a security policy is being developed. It’s possible to protect critical data from coming into and leaving the company through removable media with tools that monitor and control data transfers from desktops and laptops, irrespective of where users are and even when they are not connected to the corporate network.
5. Managing user privileges
Giving users unnecessary system privileges or data access rights means that if the account is misused or compromised the impact will be more severe than it needs to be. Organisations should determine what rights and privileges users need to effectively perform their duties and implement a policy of 'least privilege'.
6. Incident management
Security incident management is the process of identifying, managing, recording and analyzing security threats or incidents in real-time. It seeks to give a robust and comprehensive view of any security issues within an IT infrastructure.
7. Monitoring
Continuous or 24×7 cybersecurity monitoring through an experienced security services provider can drastically improve your threat alerts and help you spend more time on your security strategies.
8. Malware prevention
With the rise of malware attacks and the negative effects they can cause, it’s critical for users to implement measures that can protect them from malicious software. Some measures could be using Antiviruses and Anti-malware, Firewalls, Sandboxing, Email Scanning and Spam Filtering, and Browsing and Download Protection.
9. Network security
It is important to have policies and procedures implemented by a network administrator to avoid and keep track of unauthorized access, exploitation, modification, or denial of the network and network resources.
Thorgate’s Approach
Thorgate has worked with multiple healthtech companies to create digital products that are safe and can process data in a way that is not vulnerable. Here are a few examples of how Thorgate helped healthtech companies make efficient and secure digital products.
Minigrid
For Infogrid, Thorgate created an iOT platform for the hospitals in the United Kingdom (National Health Service), as well as, general infrastructure where sensors could be of use.
Internet of Things (IoT) applications use these sensors to collect data for transmission over the Internet to a cloud-based hub. The analytics software running on the cloud transforms data into actionable information for users. The key to successful implementation was to ensure that we are getting value from the information we are collecting and that it is stored safely.
In healthcare, hospitals utilise new technologies to ensure patient safety and comfort at all times. Pressure, force, and temperature sensors monitor critical parameters of a patient’s well-being. Outside hospitals, sensors are put into use in home care, where they can help the elderly to maintain an independent lifestyle for longer.
Some ways in which we ensure data security in similar projects is making security planning a much earlier part of the product design process, factoring cloud infrastructure into the security strategy for every product and implementation, paying close attention to how firmware updates are designed and carried out in a secure way, and conducting robust security testing before any IoT device is sent to market, including fuzz testing, penetration testing, and more.
HIPAA Compliant Communication Platform
The Health Insurance Portability and Accountability Act of 1996 Privacy Rule governs how healthcare organisations disclose, protect and use personal health information in the U.S. This is equally applicable to cloud services, messaging platforms, email providers and any other digital platform where sensitive personal information about patients is being exchanged.
Thorgate has been working on building HIPAA compliant apps where locally stored data is encrypted. Encryption key in these cases is related with the user session. API calls using modern crypto algorithms and through https (certificate pinning). Also, file data is logged through filters.
With the communication platform Thorgate built called TXP Chat, the following steps were in focus:
1. No personal data is logged, and patient data is not stored in plain text
2. All data is removed when the app is uninstalled
3. Users are automatically logged out of the application after 8 hours of inactivity
4. Media files are stored in S3 and accessed via authorisation proxy
As a result, TXP Chat™ could concentrate on the vital aspects of product development, while Thorgate took care of the details surrounding privacy and app security.
What can you do next?
If you are a healthtech company or in any other industry where data breaches seem to be inevitable, and you are looking for secure digital products to either improve efficiency in your operations or to commercialize your product, look for experienced companies like Thorgate to partner with.
If you partner with Thorgate, you can have your product developed in an ecosystem which is rich in knowledge and information so you get the best quality as a result.


